Juggernaut Firewall can block limited types of DDoS attacks on your server.
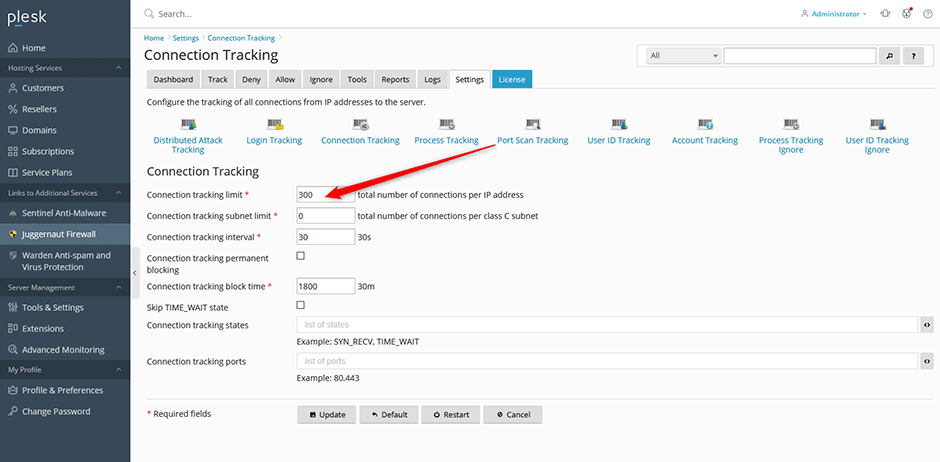
To Block Too Many Connections
Enable the tracking of all connections from IP addresses to the server. If the total number of connections is greater than this option then the offending IP address is blocked. This can help stop some types of DOS attack. To disable this option set to 0. Warning: Do not set this number too low. A recommended setting would be around 250-400.
- Navigate to Juggernaut Firewall -> Settings -> Login Failure Daemon -> Tracking Settings -> Connection Tracking
- Set the Connection tracking limit to something like 250-400. If you want to limit connection tracking to specific ports (e.g. so FTP connections are not counted) then fill in the ports 80,443 under Connection tracking ports.
- Click the Update button to save your settings.
- Click the Restart button to restart the firewall and login failure daemon.
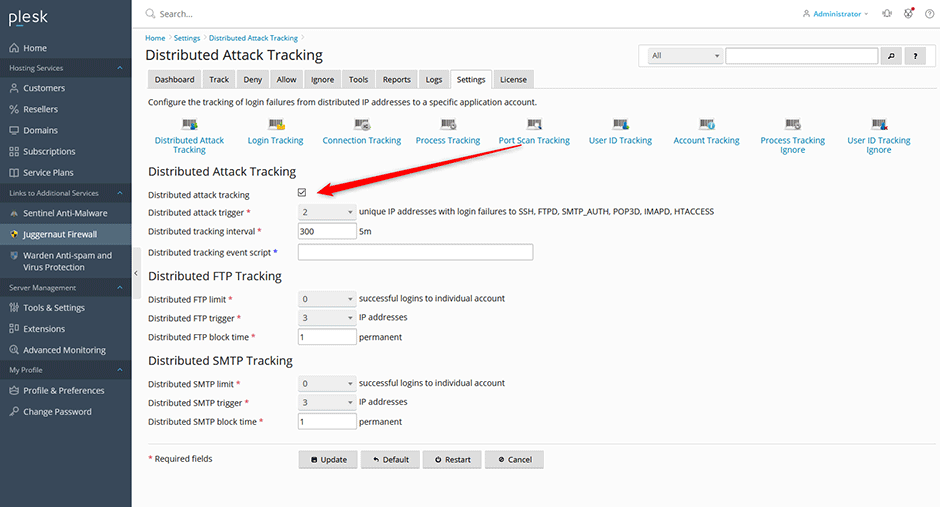
To Block Distributed Attacks
Enable the tracking of login failures from distributed IP addresses to a specific application account. If the number of failures matches the application trigger then all of the IP addresses involved in the attack will be blocked. Tracking applies to LF_SSHD, LF_FTPD, LF_SMTPAUTH, LF_POP3D, LF_IMAPD, LF_HTACCESS.
- Navigate to Juggernaut Firewall -> Settings -> Login Failure Daemon -> Tracking Settings -> Distributed Attack Tracking
- Check the Distributed Attack Tracking option to enable it.
- Click the Update button to save your settings.
- Click the Restart button to restart the firewall and login failure daemon.
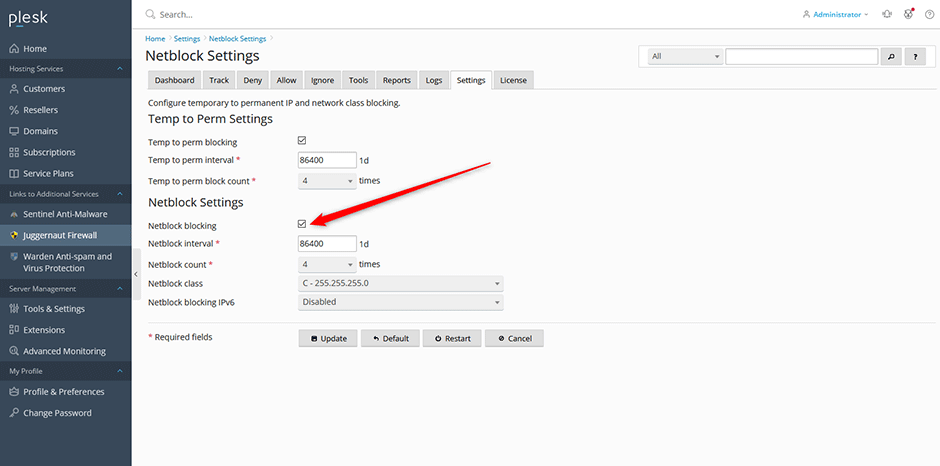
To Block Networks that Attack you Repeatedly
Permanently block IPs by network class. Permanently block classes of IP address where individual IP addresses within the same class LF_NETBLOCK_CLASS have already been blocked more than LF_NETBLOCK_COUNT times in the last LF_NETBLOCK_INTERVAL seconds. This can help blocking DDOS attacks launched from within the same network class.
- Navigate to Juggernaut Firewall -> Settings -> Login Failure Daemon -> Netblock Settings
- Check the Netblock blocking option to enable it.
- Click the Update button to save your settings.
- Click the Restart button to restart the firewall and login failure daemon.
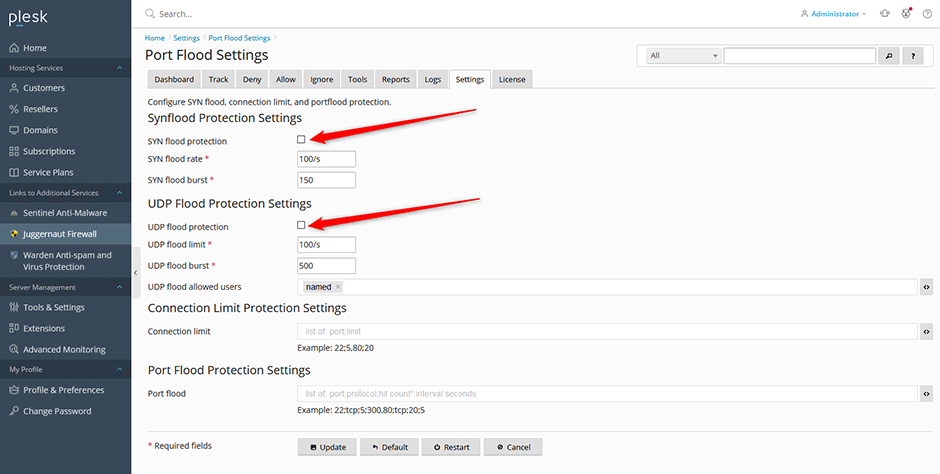
To Block SYN Flood and UDP Food Attacks
Enable SYN Flood Protection (This should only be enabled during the attack as leaving these on will slow down the server). This option configures iptables to offer some protection from tcp SYN packet DOS attempts. This option will slow down all new connections from any IP address to the server if triggered so it should only be enabled if you are under a SYN flood attack.
Enable outgoing UDP Flood Protection. This option limits outbound UDP packet floods. These usually are from from exploit scripts uploaded through vulnerable web scripts. If you use services that utilize high levels of UDP outbound traffic, such as SNMP you will need to adjust UDPFLOOD_LIMIT and UDPFLOOD_BURST options accordingly.
- Navigate to Juggernaut Firewall -> Settings -> Firewall -> Port Flood Settings
- Check the SYN flood and UDP flood protection check boxes to enable them (these should be disabled after the attack is over).
- Click the Update button to save your settings.
- Click the Restart button to restart the firewall and login failure daemon.