We are pleased to announce the release of Juggernaut Security and Firewall 3.02 under General Availability. All users are encouraged to upgrade. This release has passed Plesk certification and is now available in the Plesk extension directory.
AbuseIPDB Support
AbuseIPDB is the gold standard for abuse reporting and is used by some of the largest hosting companies worldwide. AbuseIPDB block lists get updated automatically, so your server always has the most up to date threat information. Now admins can use AbuseIPDB to check and report IP addresses for abuse. AbuseIPDB is free for up to 1000 checks per day. See here for information about how to enable AbuseIPDB reputation lookups and here for how to enable the AbuseIPDB blocklist.
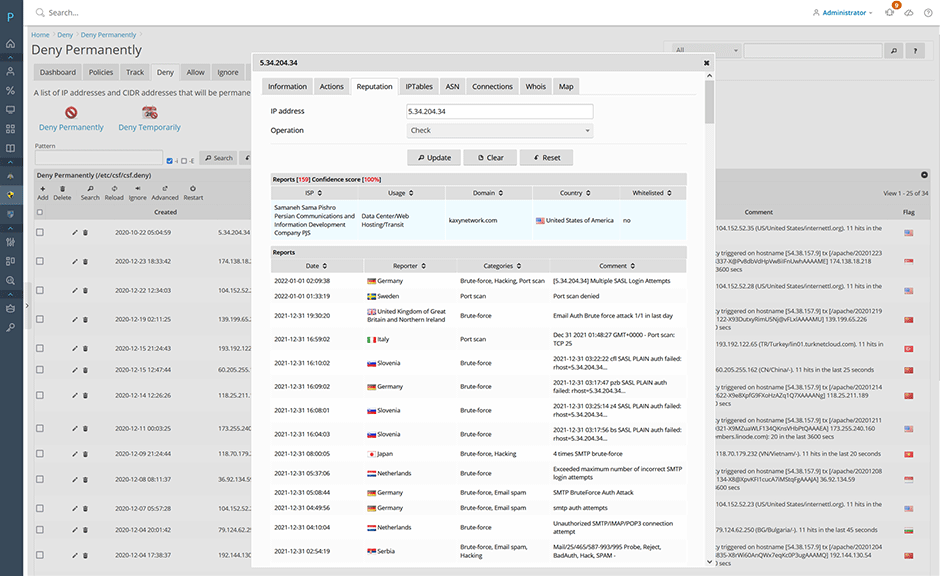
Users can report an IP address as abusive to AbuseIPDB from within the Juggernaut Firewall interface. AbuseIPDB provides free blocklists so everyone can benefit from your reports.
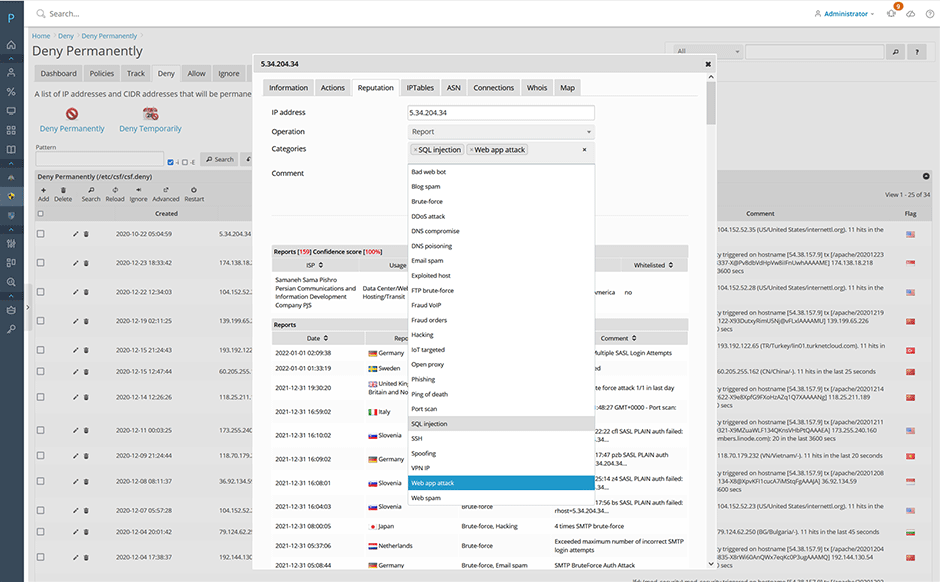
If an attack occurs on a server with the AbuseIPDB block reporting enabled, it will be reported back to AbuseIPDB which will add it to their block lists once it has reached a certain abuse confidence threshold. The strength of AbuseIPDB is that every server is sharing attack information. With every new user, abuse reporting gets more accurate, and the defense network grows stronger.
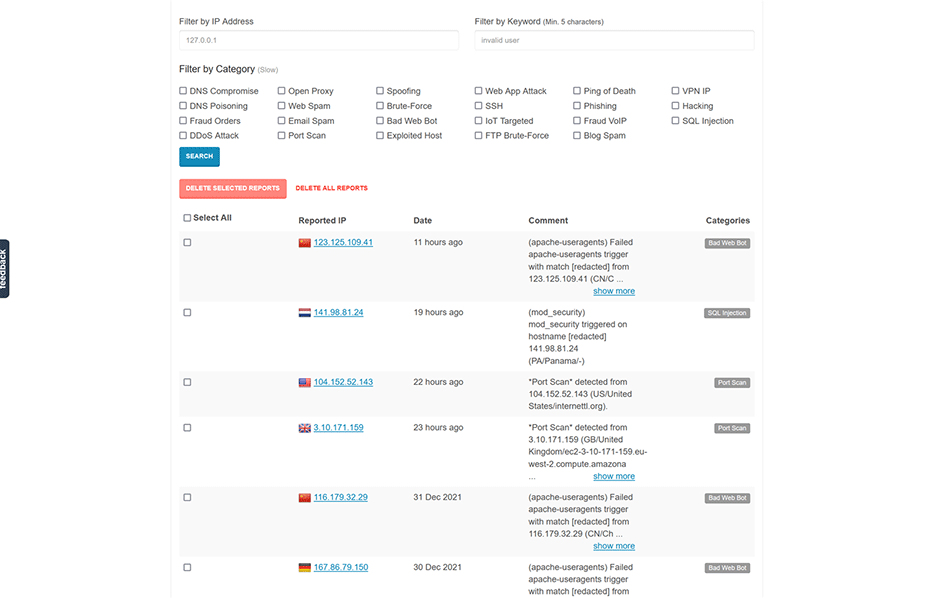
Blocklists Updated
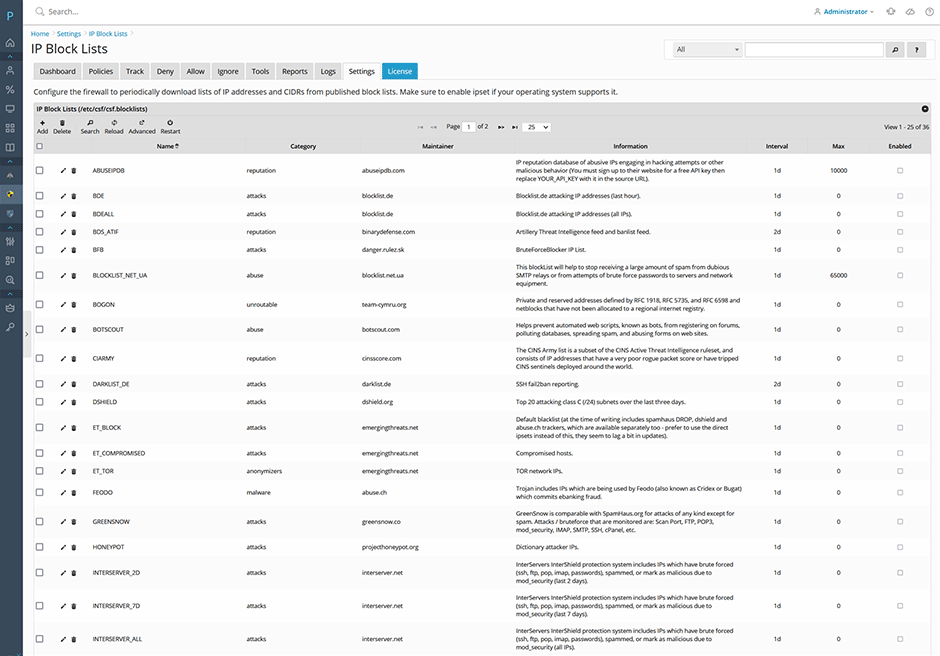
We've updated the default blocklists to remove outdated lists and switched all sources to use https://. We've also added new high quality blocklists from AbuseIPDB and InterServer. It is recommended to reset your blocklists by going to Settings -> IP Block Lists -> press the Advanced button on the grid then press the default button. Then re-enable the new blocklists that you want. See here for more information.
Changelog
[+] Added support for Rocky Linux.
[+] Added AbuseIPDB support. AbuseIPDB is the gold standard for abuse reporting and is used by some of the largest hosting companies worldwide. When enabled the login failure daemon will report blocked IP addresses to AbuseIPDB automatically.
[+] Added a reputation tab to the IP address lookup tools. Now admins can use AbuseIPDB to check and report IP addresses for abuse. AbuseIPDB is free for up to 1000 checks per day. See here for more information.
[+] Added new high quality blocklists from AbuseIPDB and InterServer for servers which have brute forced (ssh, ftp, pop, imap, passwords), spammed, or been marked as malicious due to mod_security. See here for more information.
[+] Added new abuseipdb_key and abuseipdb_block_reporting options to the installer command line interface.
[+] Added additional pre-install checks to make sure the server hardware is supported.
[=] Updated the geolocation settings page to not throw an error when first entering the MaxMind license key because new keys can take about 30 minutes before they are recognized.
[=] Updated the default blocklists to remove outdated lists and switched all sources to use https://. It is recommended to reset your blocklists by going to Settings -> IP Block Lists -> press the Advanced button on the grid then press the default button. Then re-enable the new blocklists that you want. After upgrading any removed block lists will be marked as custom and are safe to delete.
[=] Updated blocklist max defaults on large blocklists to be smaller than the default Ipset maxelem setting so that we do not cause any ipset errors when we enable the blocklist.
[=] Updated the installer to not install the net-tools package because CSF supports the newer ip binary instead.
[=] Updated the default option Netblock blocking LF_NETBLOCK to be enabled by default.
[=] Updated the default option Connection tracking limit CT_LIMIT to 500.
[=] Updated the default options DENY_IP_LIMIT to 2000 and DENY_TEMP_IP_LIMIT to 1000.
[=] Improved the denied IP address detection on the tracking pages.
[=] Updated the extension custom button location for admins, resellers, and customers to all display in the left navigation (in both service provider and power user views).
[=] Updated the IP blocklists to be on the main settings page for easier access.
[=] Updated the IMAP/POP3 and SMTP Auth logs grids to highlight important rows.
[-] Fixed a bug on the login log page where the all options were not selectable after the initial search.
To Upgrade
The upgrade is available to all active license holders. Login to your Plesk panel and click on Extensions -> Updates -> Select the Juggernaut Security and Firewall extension then press the update button. You can view the upgrade process using the command: tail -f /var/log/plesk/panel.log
Full changelog
https://docs.danami.com/juggernaut/basics/changelog
Product Information
https://www.danami.com/products/plesk-extensions/juggernaut-security-and-firewall
Четверг, Январь 27, 2022

